Penetration Test
Partner or auditor asking for a pentest?
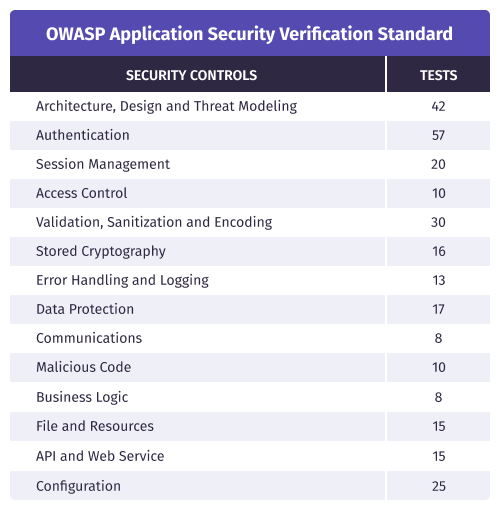
Federacy Assessments can satisfy compliance requirements or provide an initial view of security posture, utilizing the OWASP Top 10, Testing Guide, and/or Application Security Verification Standard.